What is an Enabler?
A flexible firewall allow rule that overrides DTTS®. Since DTTS® does not permit IP communication directly to a destination without resolving it by DNS first, an Enabler facilitates such a connection, especially when it’s the only way for an app or service to function.
Why are Enablers needed?
Application developers sometimes choose direct-by-IP communications, not using DNS, for services that need to survive DNS outages, accelerate connection criteria, etc. Some developers expect that they’re gaining a security advantage by avoiding the possibility of DNS poisoning attacks.
Examples of applications requiring an Enabler for some functionality
- Some Voice and Video calling/conference applications (WhatsApp, Google Meet, Snapchat Voice, Discord calls, RingCentral)
- WhatsApp also uses direct-by-IP communications for endpoints to reach their Content Delivery Network (CDN) servers
- Apple iOS components such as FaceTime and ABM/MDM functions
- PBX systems maintaining SIP trunk persistence, or for RTP traffic via other networks
- Applications using various public cloud providers for domain fronting to circumvent DNS-based filtering (e.g. Telegram)
- Internet-of-Things (IoT) devices using public clouds for fast UDP-based event notifications, video streams, audio streams such as Ring Video doorbells
- Retail VPN providers (NordVPN, ExpressVPN, Betternet, Psiphon, etc) will use direct-by-IP communications in an effort to circumvent VPN blockers
- Vendor-managed industrial equipment that require a VPN connection to vendor HQ for support sessions
- Headless equipment reaching out to various NTP servers during the startup sequence, and via cronjobs/scheduled tasks
Many of these apps don’t use direct-by-IP communications exclusively, but may require an enabler for some functionality. As apps modernize, fewer and fewer require Enablers. For example, Netflix and Lynda used to require them for their CDNs but no longer do so.
Quick Reference of known applications
| Application - Function | Requires Enabler | No Enabler needed | Notes |
|---|---|---|---|
| iPhone (iOS) | — | Requires Enabler for FaceTime and ABM/MDM functions | |
| Google Meet | — | Requires Enabler for video conferencing | |
| Telegram | — | Requires Enabler for all functions | |
| — | Requires Enabler for pictures/video attachments as well as voice/video calls via STUN | ||
| zoom.us video conferencing | — | Performance is enhanced with an Enabler, but not required | |
| Google Workspace | — | Not needed | |
| Microsoft Office - any version | — | Not needed | |
| Microsoft Teams | — | Not needed | |
| Netflix | — | Not needed | |
| YouTube | — | Not needed | |
| Social Media apps (in general) | — | Not needed |
How to use Official Enablers
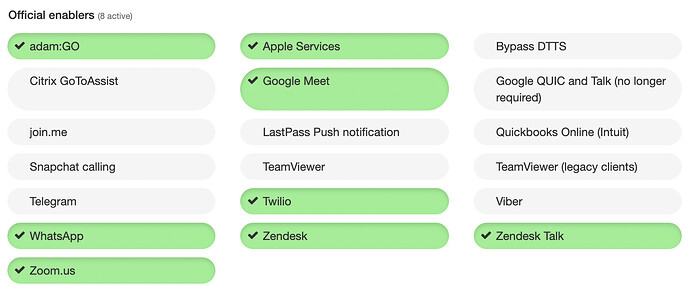
On your dashboard.adamnet.works, provided you are on a subscription plan with DTTS®, you will see Official Enablers on each policy like this:
When in green, they’re enabled, otherwise they’re disabled.
How to build your own Enabler
From your dashboard → Manage Rules → My Rules → Enabler (tab)
Determine the parameters of destination host/network block, [s]ource or [d]estination, [u]dp or [t]cp as well as port ranges. For example, to reach:
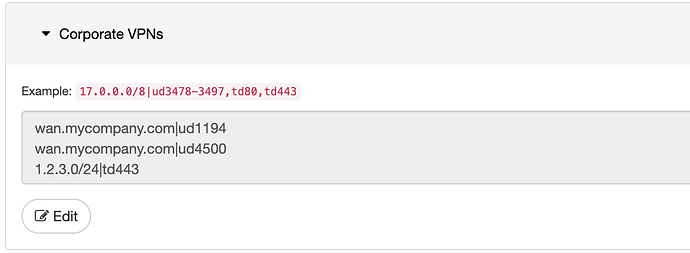
wan.mycompany.comUDP destination port 1194 (for OpenVPN connections)wan.mycompany.comUDP destination port 4500 (for IPSEC VPN persistence)1.2.3.4/24TCP port 443 (for various public https services)
The Enabler would look like this:
Note that hostnames will regularly be resolved by the adam:ONE® gateway itself and keep those destinations available without requiring an DNS entry to open the hole.
Then, of course, that Enabler needs to be turned on for each respective policy where it applies.
For IP protocols other than TCP/UDP
In the event any other protocol is required, it can be done on the adam:ONE® router platforms. In the case pfSense®, a firewall allow rule can be created for ICMP, for example, if required.
Legacy note
Prior to adam:ONE® version 4, Enablers were done manually via pfSense rules. Some significant advantages exist with a dashboard approach. We strongly recommend any pfSense manual allow rules be converted to dashboard enablers.