Scope of this document
The purpose and scope of this document is limited to a network environment where these conditions are met:
- Active Directory is integral to the network, but ADAM is running in standalone or gateway mode
- adam:ONE® is self-managed (on managed sites, all these settings apply, except DHCP remains on the gateway, not on domain controllers)
Summary of Best Settings
| DHCP Server: | Active Directory |
|---|---|
| DHCP Options: | Gateway: ADAM host |
| DNS: | ADAM host(s) |
| Other options: | as required by environment |
| Forwarding list: | your internal domain.local |
| Forwarding list redirected to: | Active Directory |
| Forwarding list turned on: | All Rulesets (including Unfiltered ones) |
Example configuration:
| Company Internet domain: | yourcompany.com |
|---|---|
| Company internal domain: | your internal domain.local |
| IPv4 subnet: | 10.20.30.0/0 (10.20.30.0/255.255.255.0) |
| ADAM LAN IP: | 10.20.30.1 |
| Active Directory Server IP: | 10.20.30.10 |
| DHCP Scope: | 10.20.30.100-199 |
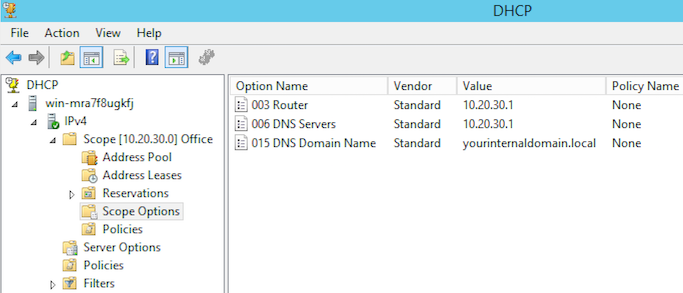
| DHCP Option of Gateway: | 10.20.30.1 |
| DHCP Option of DNS Server(s): | 10.20.30.1 (be sure not to specify 10.20.30.10 as secondary) |
| Forwarding list of “Internal domains” : | yourinternaldomain.com |
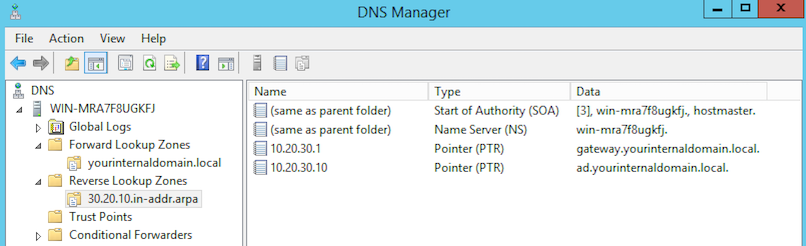
| 30.20.10.in-addr.arpa | |
| Forwarding list re-directed to: | 10.20.30.10 |
| DHCP running on ADAM host: | NO |
| DHCP running on Active Directory Server: | YES |
Configuration Details
This is what a Forwarding list looks like on your dashboard.adamnet.works → Manage Rules → My Rules
Rule should be turned on for all Rulesets.
Windows 2012 DHCP Server configuration
Windows 2012 DNS Server configuration for yourinternaldomain.local and Reverse DNS
Redundancy Recommendation
When devices have primary and secondary DNS servers, unlike the common perception, the secondary is not a backup DNS server per se. Instead, DNS clients typically issue the same query to all DNS servers received via DHCP at the same time. For this reason, you do not want a primary DNS server of ADAM host and a secondary of AD.
Instead, to achieve redundancy and business continuity for a ADAM environment, you want to have two instances running simultaneously with the same configuration. It’s worth pointing out that the second ADAM instance could be in private server/standalone mode if the first ADAM instance is in gateway mode.
Also in configuration of multiple AD controllers, the DNS settings on the AD servers themselves should be as follows:
| SERVER | DNS settings on IP configuration |
|---|---|
| ADC1 | localhost (only) |
| ADC2 | localhost (only) |
| For example, if AD1 is a host at 10.20.30.10 and ADC2 is 10.20.30.11, the settings would be as follows: |
| SERVER | DNS Settings |
|---|---|
| ADC1 | 127.0.0.1 |
| ADC2 | 127.0.0.1 |
During AD Controller configuration you may need to briefly set the server’s adaptor DNS settings to another domain controller’s IP, but upon configuration it must be changed to 127.0.0.1. This is so that all upstream queries go directly to the gateway in case DTTS is enabled. DTTS short-lived allow rules are only opened for the query source.
At the time of this writing, this can be achieved via support@adamnet.works to assist multiple BoxIDs at the same location. In the future, this process will be automated and part of the UI.
Benefits of the above suggested configuration:
The advantages of this configuration over having devices all make DNS queries directly to AD are numerous:
- Offloads DNS load from AD to the gateway for queries that AD would be forwarding upstream anyway.
- Allows ADAM per-device filtering to work. (When devices go to AD first for DNS answers, ADAM is unaware of the query’s origin, so per-device filtering couldn’t work in an AD-first scenario)
- All AD and PTR record functionality is maintained and DHCP/DNS on AD is optimized, requiring answers only for itself.
- Allows you to provide additional security for AD servers by building a “Microsoft Essentials” whitelist only, which allows it to obtain Windows updates, but otherwise makes use of the fact that it’s on a whitelist from an Internet access perspective.
- Protects against DNS Server attacks such as SIGRed.