adam:GO™ is a security stack that extends Zero Trust connectivity (ZTc) to multi-homed devices. Multi-homed devices have multiple ways to connect to the internet: Cellular, WiFi, Ethernet.
ZTc is achieved with a secure IPSec tunnel from an endpoint to the designated and dedicated client cloud exit(s).
The three most common variations (on iOS) look similar but behave differently as shown below.
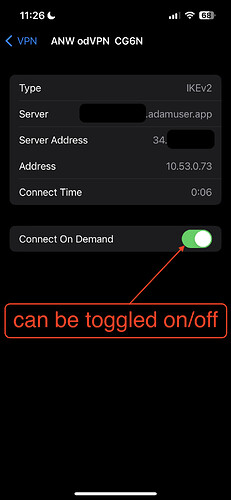
On-demand
- Single tunnel on currently-preferred connection (WiFi, if available, otherwise over Cellular)
- Can be turned on/off on-demand
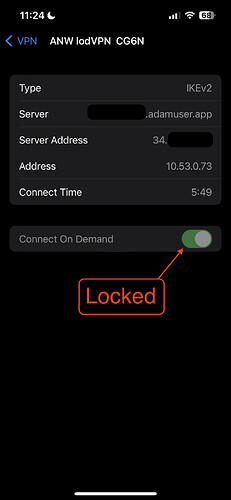
Locked On-demand
- Single tunnel on currently-preferred connection (WiFi, if available, otherwise over Cellular)
- Cannot be turned off on-demand
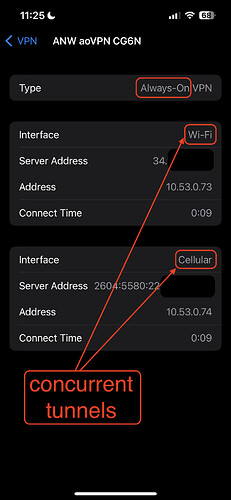
Always-on
- Dual tunnel on WiFi and Cellular, using iOS multipath TCP
- No toggle exists and can only be used with a supervised iOS device
adam:GO™ includes essential building blocks such as Mobile Device Management and Device Supervision. This is how a number of options are available and compared below:
| Feature | On-demand | Locked On-demand | Always-ON |
|---|---|---|---|
| iOS Device user can toggle on/off | Yes | No | No |
| Secure Tunnel Payload auto-installs after factory-reset | Yes | Yes | Yes |
| Android Device user can toggle on/off | No | ||
| macOS non-administrative user can toggle on/off | Yes | No | No |
| macOS administrative user can toggle on/off | Yes | Yes | Yes |
| Windows non-administrative user can toggle on/off | Yes | No | |
| Windows administrative user can toggle on/off | Yes | Yes | |
| Can be used in conjunction with other iOS tunnels* | Yes | No | No |
| Can be used in conjunction with other macOS tunnels | Yes | Yes | Yes |
| Can be used in conjunction with other Windows tunnels | Yes | Yes | Yes |
| Works on most public WiFi hotspots | Yes | Yes | See notes |
| iOS AirDrop compatibility | Yes | Yes | No |
| iOS CarPlay compatibility | Yes | Yes | No |
| iOS Apple Watch compatibility | Yes | Yes | No |
| iOS MMS messages | Yes | Yes | No |
| iOS WiFi LAN access compatibility | Yes | Yes | No |
| iOS Apple ScreenSharing Support | Yes | Yes | No |
| iOS IPSec WiFi Calling Support | Yes | Yes | Yes |
| iOS IPSec Dual Concurrent Tunnel WiFi and Cellular** | No | No | Yes |
| iOS tunnel authentication failure | Fails Open | Fails Open | Fails Closed |
| iOS tunnel host unreachability | Fails Open | Fails Closed*** | Fails Closed*** |
*1 Multiple on-demand tunnels can be provisioned but iOS permits the use of only one tunnel at a time
**2 Makes for smoother WiFi-to-Cellular and Cellular-to-WiFi transitions
***3 Symptoms include inability to use Guest WiFi if IPSec host, UDP port 500 and/or 4500 are blocked
All adam:GO™ secure tunnels are full tunnels and become the default route on the mobile operating system. However, by design there are some domains and destinations that are split outside of the tunnel, including:
| Domains bypassing tunnel | Purpose |
|---|---|
captive.apple.com |
iOS Captive Portal Detection |
[fqdn-to-IPSec-host] |
Establish IPSec tunnel |
lcdn-locator.apple.com |
iOS MDM functions |
configuration.ls.apple.com |
iOS MDM functions |
gsp[*]-ssl.ls.apple.com |
iOS MDM functions |
[*].3gppnetwork.org |
Mobile calling over WiFi in use by most cellular carriers, domain used for a concurrent split tunnel to carrier for mobile SIP services |
Additional notes
For a typical on-demand iOS connection, even when locked, there is other traffic which connects to Apple directly, prior to the tunnel being established. Typically the sequence after power-up of an iOS device that auto-connects to a previously-known SSID is like this:
time.apple.com
gdmf.apple.com
init.push.apple.com
comm-main.ess.apple.com
pds-init.ess.apple.com
captive.apple.com
gateway.icloud.com
gsp85-ssl.ls.apple.com
gspe35-ssl.ls.apple.com
10-courier.push.apple.com
cl3.apple.com
comm-cohort.ess.apple.com
mesu.apple.com
stocks-data-service.apple.com
app-site-association.cdn-apple.com
acsegateway.icloud.com
gspe1-ssl.ls.apple.com
weather-data.apple.com
ocsp.digicert.com
lcdn-locator.apple.com
[client-subdomain].adamuser.app
However, with an Always-on tunnel, the list is much shorter and only contains:
[client-subdomain].adamuser.app
gspe1-ssl.ls.apple.com
As it turns out, if gspe1-ssl.ls.apple.com and other domains operating outside the tunnel are disallowed at the WiFi gateway, iOS functionality is not impacted. This additional step would be necessary in order to truly have all traffic connect via the always-on tunnel.