DNS rebinding is a method of using public DNS records, such as localhost.fictitious.io to resolve to a private rfc1918 IP address, such as 127.0.0.1, for example. This can then be used in an attack.
adam:ONE® offers protection against DNS rebinding by default with this config option included at installation time:
private-subnets=0.0.0.0/8,10.0.0.0/8,127.0.0.0/8,172.16.0.0/12,169.254.0.0/16,192.168.0.0/16,fd00::/8,fe80::/10,::ffff:0:0/96
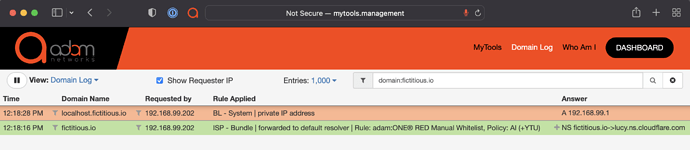
Using the above example, if a given application needs to function with it, using public DNS services, by default DNS rebind protection would show the following in your mytools.management/log:
The BL - System | private IP address indicates that DNS rebind protection prevented it from resolving to 127.0.0.1.
Managing Exceptions
There are many real-life applications that interact with a local web services. For such domains, there’s a simple way to manage exceptions without disabling DNS rebinding protection altogether.
-
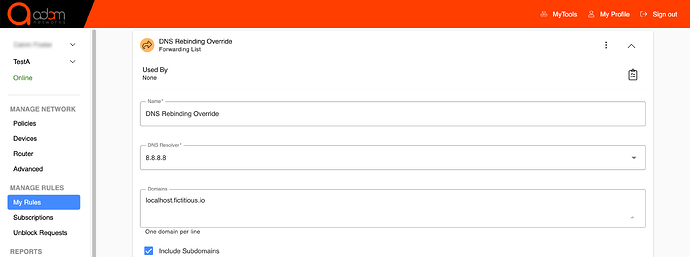
Create a rule of type Forwarding Rule from the dashboard → My Rules → Add List → List Type: Forwarding List, and forward the required domain to 8.8.8.8, which is a public resolver that never filters any FQDN:
-
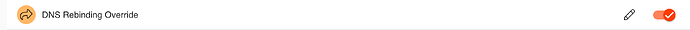
Enable the rule on all policies that require it:
-
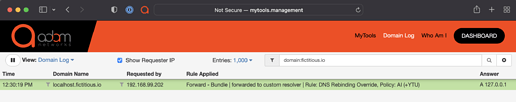
Run the same query again and confirm it resolves:
% dig localhost.fictitious.io +short
127.0.0.1