Background
A core tenet in Zero Trust Connectivity is the Principle of Least Privilege. From a security point of view, you want a newly-discovered device to be unable to reach out of its network segment, never mind out to the internet where a Command & Control operator may be waiting for its connection.
However, modern-day devices always check for connectivity before the rest of the networking stack and applications begin. This is where a Holding Tank applies, which is a label we apply to a Zero Trust policy that passes a connectivity check, and nothing else.
This is a practical way of inventorying newly-discovered devices that can then easily be identified and applied to the desired target policy.
Setting up a Holding Tank Policy
-
Subscribe to this User Subscription containing connectivity check domains used by most modern operating systems including Android, iOS, Windows, macOS, ChromeOS and many Linux variants. To Subscribe means you will receive automatic updates to this subscription. Make a copy creates a one-time copy only:
-
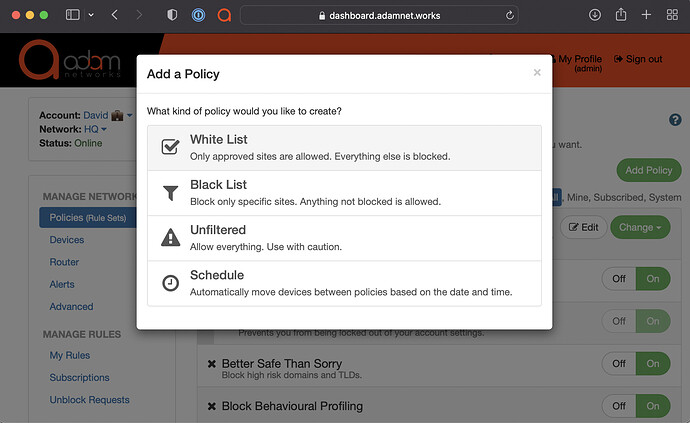
Next, go to Policies → New Policy → Type create a new policy of type Allow List (White list) and call it Holding Tank Policy (or an alternative name of your choice):
-
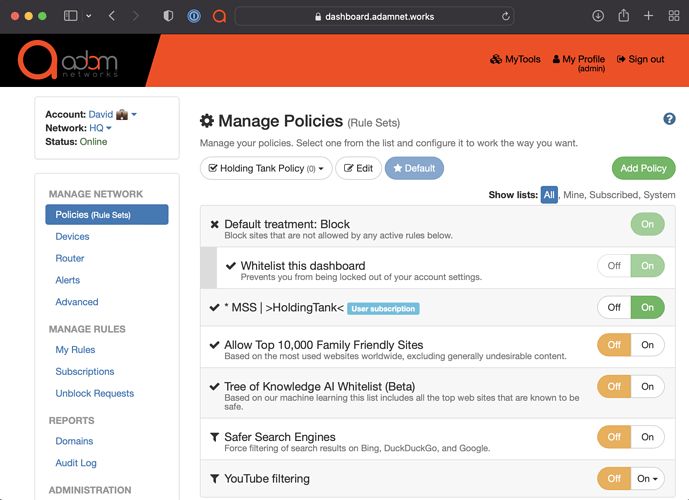
Leave everything turned Off except for
* MSS | >HoldingTank<: -
Click on Make Default (to the right of the Policy Name Edit button)
Any newly-observed devices will automatically be treated with your default policy of the Holding Tank.
This is a powerful method of IR (Incident Response) process to connect potentially still-infected devices more safely, especially if still isolated from all safe and sanitized devices. For example, AD controllers, when on separate network segments, would be inaccessible to devices while they’re in the holding tank, keeping AD safe.
Additional notes
The end-user experience is such that the device sees no captive portal, but also is unable to access any website or service outside the domains listed on the subscribed rule/list above. It is strongly advised that any potentially-affected users are aware of this treatment on any network where this applies.
Furthermore, if this is applied to network segments used by smartphones, you will want to use Mobile Device Management (MDM) platform to turn off Private MACs, or advise authorized users to do so first, see adamnet.io/macrandom.
If new connectivity testing domains are discovered that are not part of this subscription yet, please feel free to request them to be added via support@adamnet.works.
Managed Services
As of 2022, this is the standard deployment for all new/renewed managed clients.