Fighting desktop email client phishing attack surface is improving to the point where a lot of phishing sites need a single SafeBrowsing-equipped browser (Chrome, Safari, etc) submit meta-data to centralized threat intelligence service, which can detect and immediately protect every other SafeBrowsing-equipped user. Furthermore, Security Awareness Training, has helped users be somewhat more cautious in clicking links.
However, the malicious actors aren’t idly standing by as they watch their phishing site go undetected-as-bad from months, to weeks, to days, to only hours or minutes-long life in many cases.
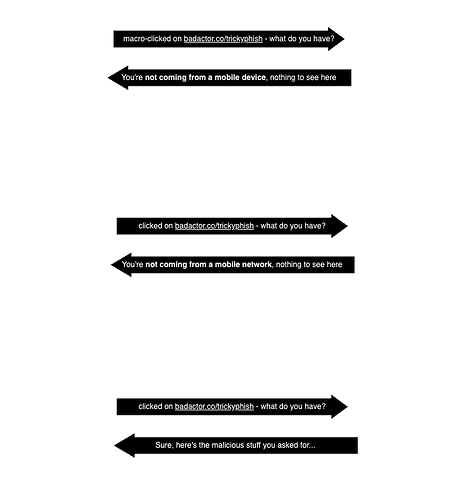
In our own experience we now see that malicious actors have extended their phishing sites’ lifetime by applying two key techniques:
- Block all IP connections unless they come from carrier-owned IP space. This turns out to represent the vast majority of sandboxes that crawl the internet for threats or threat verifications.
- Block all non-mobile user agents, or screen resolutions that aren’t likely a mobile device.
These two techniques makes it so that the VirusTotals of the world have a difficult time detecting a phishing site.
However, with Zero Trust connectivity, there are now multiple layers of protection that protects a mobile device no matter how or where it connects: