Psiphon is a powerful tool if you’re in a nation state that censors your Internet connection. It serves a great purpose for freedom when you need it. Unfortunately, it also can be a tool by bad actors to exfiltrate data and hide in plain sight by circumventing traditional internet security gateway protection.
adam:ONE™ can successfully block Psiphon. Keep in mind that it does require correct setup in your whole networking ecosystem. In short, if you make a mistake with permissive firewall rules, misconfiguration, running open proxies or any operator errors, there is a good chance that Psiphon can get through. If you are in need of blocking Psiphon, we highly recommend you use a licensed MSSP to ensure your network protection is properly configured.
To block Psiphon with adam:ONE™, follow these steps:
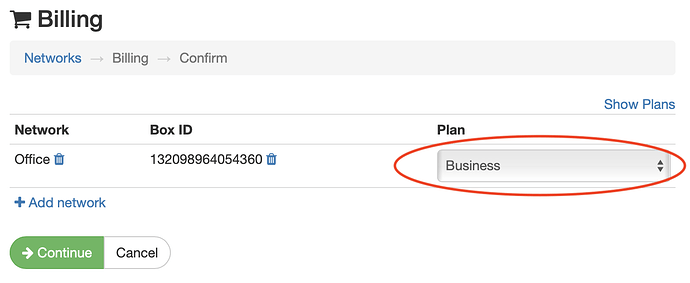
- Confirm you’re on a Business or Enterprise subscription as the necessary features are not available on Essentials and Professional plans. You can do this on your dashboard -> Billing Settings -> Change Networks and select the Business plan.
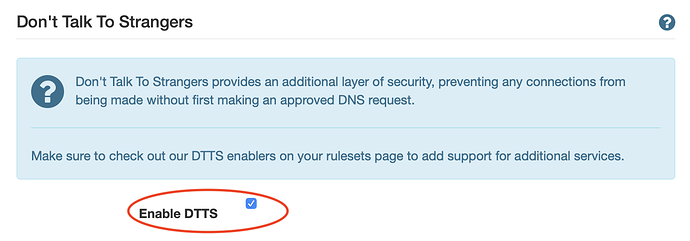
- Enable your DTTS (Don’t Talk To Strangers) feature on your dashboard -> Advanced section.
- A special-case rule needs to be added to your dashboard. Speak to your licensed MSSP to have it provisioned. It will appear like this on all of your blacklisting and whitelisting Policies on your dashboard (make sure you turn it ON for all of your Policies where you want this protection):
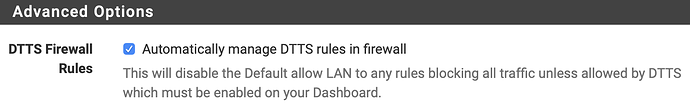
- If you’re on the pfSense platform, make sure you either disable the “Default allow LAN to any rule” in Firewall -> Rules menu. On most implementations, we recommend having the firewall rules managed by our service with this setting: Under Services → DNSthingy
-
Make sure you do not have “Bypass DTTS” enabled on the Policy you want to have Psiphon blocked.
-
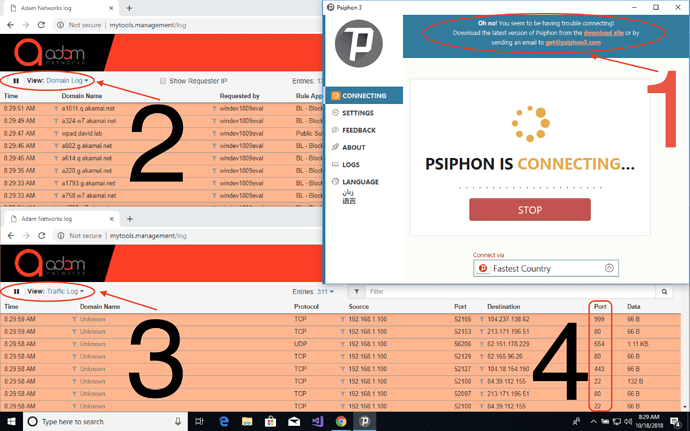
To verify it is working, observe two separate logs, in two separate browser windows, at http://mytools.management/log which are accessible only from within your network and only for authorized devices in your Dashboard’s Manage Policies -> Devices listing:
Legend:
- Shows Psiphon itself reporting it is unable to connect, but this will take a few minutes to appear
- When viewing the Domain Log, you see every domain that is being attempted to connect to and being blocked as a “BL - Block Psiphon” on the Rule Applied column
- When viewing the Traffic Log from the drop-down menu, shows IP connections, most of which will be IPs that did not use DNS first
- Shows the destination ports where Psiphon would normally connect as a proxy but is unable to do so now
To see this in a video form:
Commonly-asked questions:
- What is the difference between Policies based on Whitelisting vs Blacklisting?
- Answer: If you follow the above steps, Psiphon itself will be blocked on either type Policy. However, we strongly recommend whitelisting Policies in order to block yet-unknown proxies and VPN providers
- How do you handle domains that have CNAMEs of commonly used Psiphon proxy hosts such as, www.dictionary.com which has e2374.g.akamaiedge.net as a CNAME?
- On whitelisting Policies, CNAME flattening occurs, which allows the former to resolve, if whitelisted, and the latter to be blocked.
- On blacklisting Policies, simply create a Forwarding List for domains for which to create an exemption (note that Forwarding Rules take precedence over Blacklists, so it is the best method for exemptions)
- If Psiphon is still connecting, how is that possible?
- DTTS rules only apply if no match is found in pfSense GUI firewall rules. Check to make sure no firewall allows outbound access for the network/devices you wish to Psiphon-restrict.