The DTTS (Don’t Talk To Strangers) engine operates on allowing any traffic to destination IP address(es) once a DNS query is allowed and answered.
In cases where the desired outcome is to only permit access to specific destination ports, this can be achieved by adding REJECT/BLOCK rules, which override the DTTS ALLOW rules.
For example, if the desire is to block all UDP ports + all TCP ports (except ports 80 and 443), the two block rules would look like this logically:
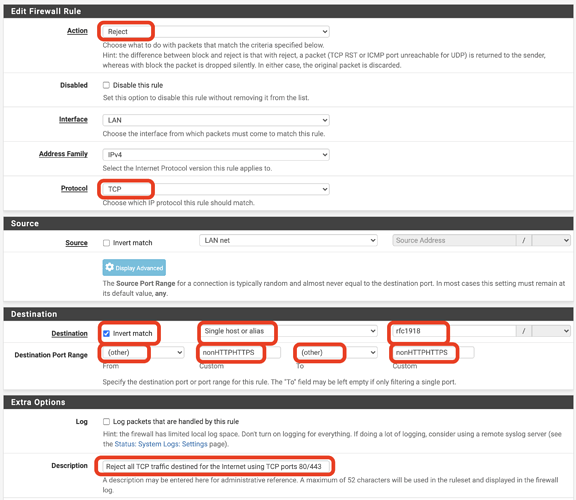
- Reject all TCP traffic destined to ports other than 80 or 443 on the Internet
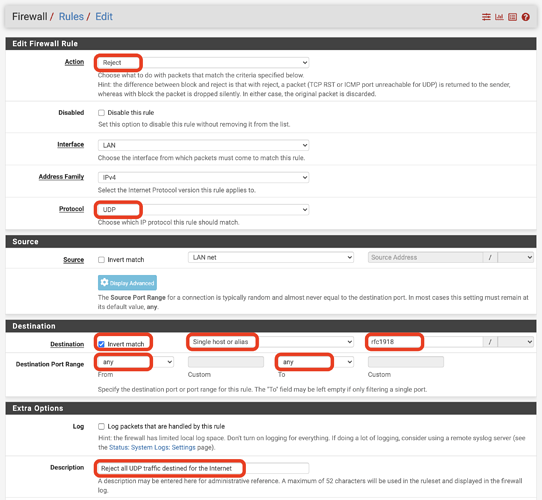
- Reject all UDP traffic destined anywhere on the Internet
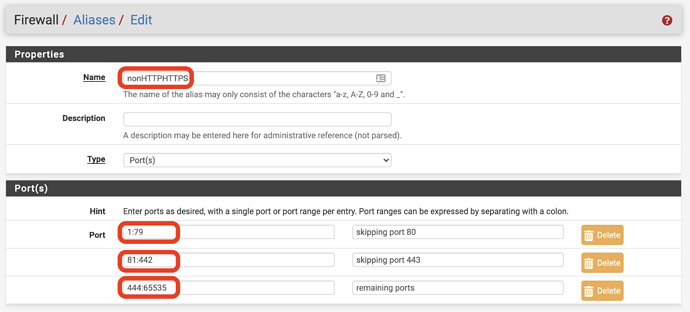
Practically speaking, on the pfSense platform you would create a PORT alias, we call it nonHTTPHTTPS like this:
Then you can apply a logical REJECT rule like this:
Likewise, to block all UDP traffic, the rule would look like this:
Using the above rules, the net result would be that a network would limit DTTS functionality to TCP port 80 and 443 as all BLOCK/REJECT rules override opening of any other ports.
Note that this specific example would also block internet-bound QUIC and NTP traffic and any other commonly used UDP service, but we understand some security requirements ask for this.