Internal domain lookups, including reverse DNS (PTR) queries often leak out to the public Internet on default gateway configurations. Not only is this unnecessary, it reveals operational details of internal networking infrastructure that is best kept private.
Many gateways and most endpoints will take the DNS suffix of a host and append it to DNS query FQDNs. For example, if your DNS suffix is home.arpa, as is often the default, an endpoint requesting a domain lookup to visit Google, will submit two queries:
google.com
google.com.home.arpa
Only the first query should go out to any upstream resolver.
PTR (Reverse DNS) records also are commonly found leaking. A typical internal host will ask for a PTR record for its gateways, e.g. 192.168.50.1 which looks like this:
PTR record for 1.50.168.192.in-addr.arpa
It is unnecessary to reveal this to the public internet because it cannot answer PTR records for rfc1918 private IP addresses. Furthermore, leaking this information is bad operational security.
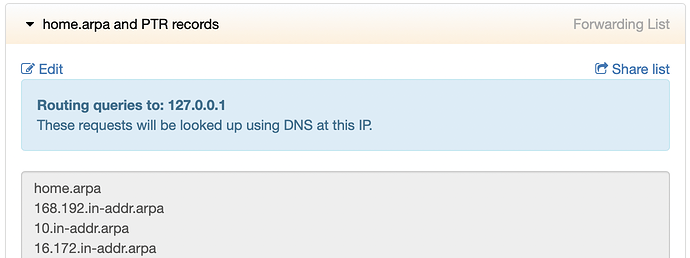
To prevent such DNS leakage, create and enable a forwarding rule (to 127.0.0.1) such as this:
You will want to use your internal domain instead of home.arpa.
The full list of domains in that rule include all rfc1918 reverse DNS network domain names:
home.arpa
10.in-addr.arpa
168.192.in-addr.arpa
16.172.in-addr.arpa
17.172.in-addr.arpa
18.172.in-addr.arpa
19.172.in-addr.arpa
20.172.in-addr.arpa
21.172.in-addr.arpa
22.172.in-addr.arpa
23.172.in-addr.arpa
24.172.in-addr.arpa
25.172.in-addr.arpa
26.172.in-addr.arpa
27.172.in-addr.arpa
28.172.in-addr.arpa
29.172.in-addr.arpa
30.172.in-addr.arpa
31.172.in-addr.arpa
For the above rule to function properly, a localhost binding will need to be provisioned. This is part of our recommended configuration.
This rule and integrated configuration is included on all MSS+ sites.