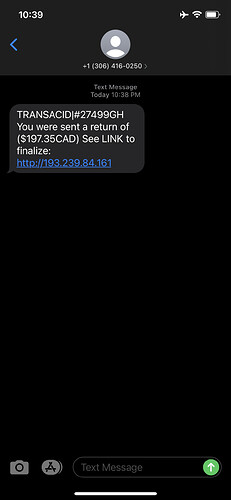
Text-based phishing, called smishing is an effective way to steal credentials from unsuspecting victims. I receive them regularly, and they look something like this:
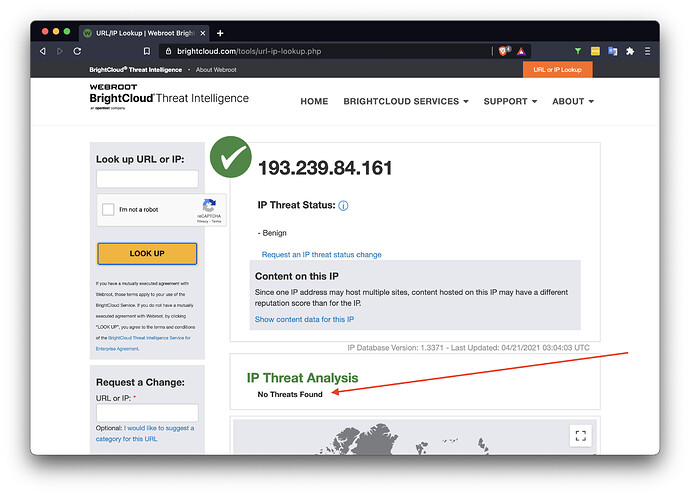
I immediately checked a few sources that are generally seen as leading edge sources on IP and domain name reputations. So I decided to check out the very reputable BrightCloud public lookup at URL/IP Lookup | Webroot BrightCloud and this is what I found:
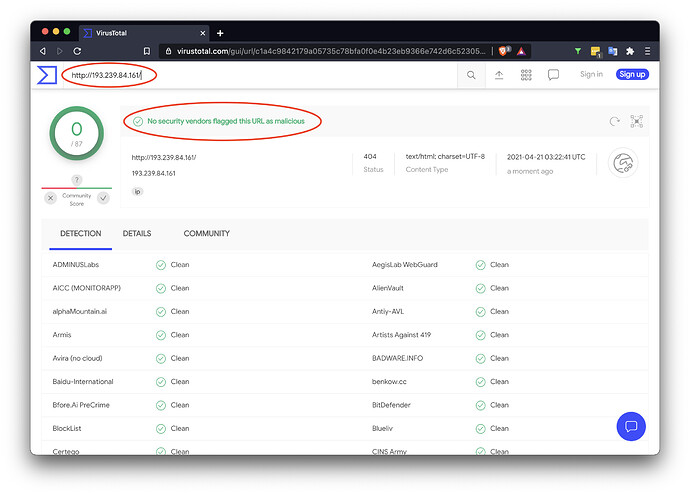
And another source so often used to check for threats is virustotal.com, where this was my result:
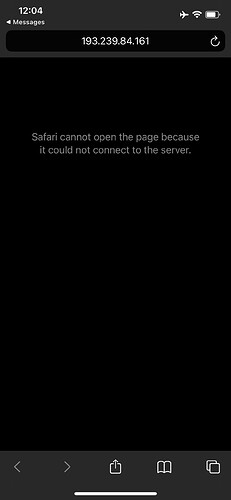
Ok, so far so good. Modern threat intelligence tells me I’m ok clicking on the link. Let’s first try on LTE. I’m on Rogers, IPv6 only, we’ve recovered from yesterday’s outage, but it just cannot connect to the site:
At this point I’m starting to wonder if this SMISHER had too much success with his site that he DDOS’d himself.
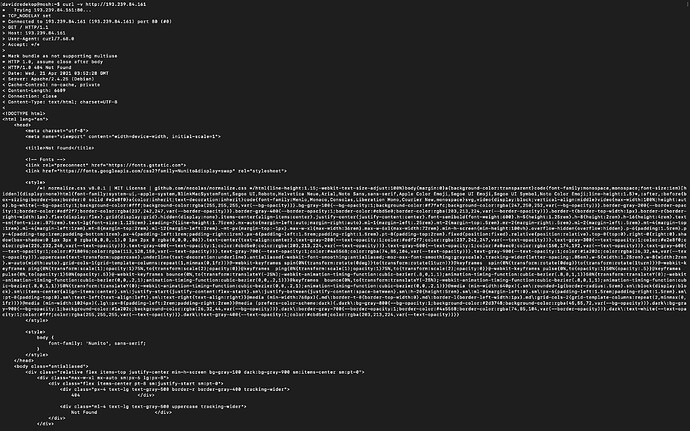
Time to check from my mosh server on IPv4 with curl -v hxxp://193.239.84.161, and sure enough, the web server is alive and serving:
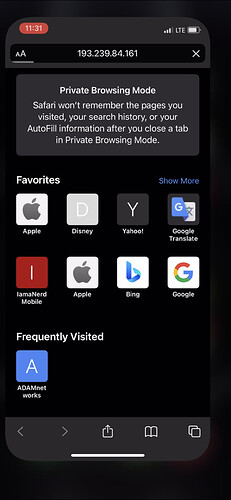
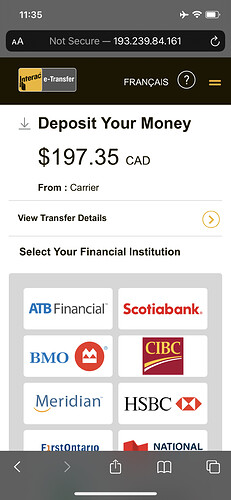
Time to try from a lab phone without any security protection:
And there you have it! A nice phishing site, purposefully avoiding detection from threat intel sources, but when a real phone from a typical Internet connection wants to connect, the thief is ready to take your banking credentials of any kind.
Google Safe Browsing didn’t block it
BrightCloud Threat Intel detected nothing, even after submission
VirusTotal’s many vendors found no threat
This is not a criticism against the above vendors. In fact, they play an ever-important role in identifying past threats and certainly make threat actors pay higher evasion prices and avoid detection. The purpose of this article is to show that traditional approaches simply just accelerate the cat-and-mouse game between threat actors and preventive measures of blocking by malicious domains or IP addresses.
However, with DTTS® (Don’t Talk To Strangers®) protection with adam:ONE® or adam:GO™, this is the result:
DTTS® simply disallows any connection that did not originate with an allowed DNS query.