What is DNS Encryption?
DNS was originally conceived as a simple, clear-text protocol where a client would ask a server “What IP address should I use for example.com?” The Server would then respond with 93.184.216.34.
A lot has happened since the birth of DNS. In the modern era, we have two key protocols that offer DNS encryption:
DNS-over-TLS
Also usually notes as DoT. This is standardized to use TCP port 853 and experiences some adoption in the open source community, in general.
DNS-over-HTTPS
Also usually written as DoH, the protocol uses HTTPS and usually runs over TCP port 443 (although it can technically be over any port). Some motivation behind this protocol was to offer end-users:
- DNS security and encryption in transit
- Interception-proof, man-in-the-middle proof
- DNS availability to anyone, anywhere
For the most part, this has been achieved, but when applying the best adam:ONE® has to offer, the recommended CISA approach is achievable, namely this logical flow:
Endpoint (encrypted DNS query) → Organization’s Secure DNS service → Recursive/Public resolver query (encrypted DNS query).
For example:
DeviceA → DoT query → 10.0.0.1:853 → recursive DoT query → 8.8.8.8:853
DeviceB → DoH query → https://doh.anycorp.io/dns-query → recursive DoH query → https://1.1.1.1/dns-query
What NOT to do:
Specifically what any security-conscious environment must consider is to disallow this scenario:
Endpoint → DoH/DoT → Public Resolvers (Google, CloudFlare, etc)
The blocking of external DNS services (enforcing internal DNS services) of any kind will be the the default when your adam:ONE® policy enforces:
- DTTS® which prevents endpoints from using public IP addresses for anything, including DoT, DoH
- Zero Trust connectivity (whitelist) policy which explicitly blocks known DoH URLs
- Even if a DoH server is found on a whitelisted domain, any IPs obtained are not reachable due to DTTS® enforcement
How to use DNS encryption with best practices
- use adam:ONE® muscle version 4.11 and later
- ensure your firewall rules are the latest standard as per adamnet.io/pfsenserules
- have a managed/commercial plan on your adam:ONE® subscription
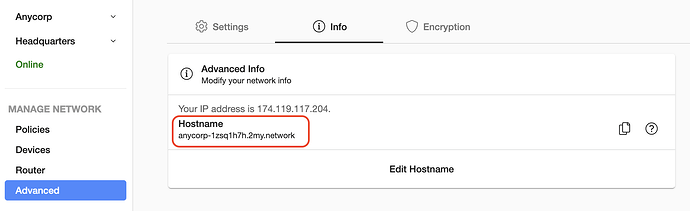
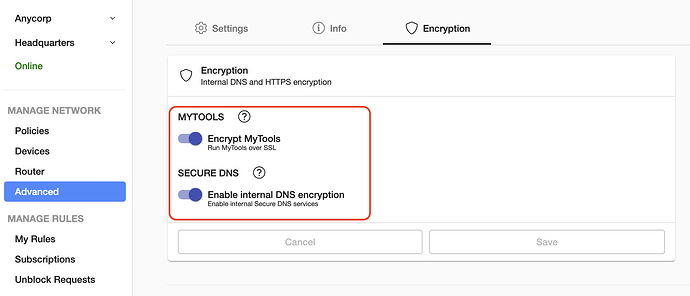
- Select your hostname and enable DNS Encryption and Secure MyTools
At that point, the muscle offers legacy DNS, DoT and DoH on all of its interfaces.
Testing DNS Encryption
RFC 9462 is a standard for Discover of Designated Resolvers. The assumption is that your DHCP server is offering the adam:ONE® gateway instance as its legacy DNS resolver, which is then asked by the endpoint to upgrade its DNS encryption.
If you’re running the latest version of dig you can test by making a SVCB type query to the gateway for host _dns.resolver.arpa like this:
[2.7.1-RELEASE][admin@gateway1.lab29.anycorp.io]/root: dig SVCB @192.168.29.251 _dns.resolver.arpa
; <<>> DiG 9.18.14 <<>> SVCB @192.168.29.251 _dns.resolver.arpa
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 7888
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;_dns.resolver.arpa. IN SVCB
;; ANSWER SECTION:
_dns.resolver.arpa. 60 IN SVCB 1 anycorp-1zsq1h7h.2my.network. alpn="h2" port=443 ipv4hint=192.168.29.251 key7="/dns-query{?dns}"
_dns.resolver.arpa. 60 IN SVCB 1 anycorp-1zsq1h7h.2my.network. alpn="dot" port=853 ipv4hint=192.168.29.251
;; Query time: 0 msec
;; SERVER: 192.168.29.251#53(192.168.29.251) (UDP)
;; WHEN: Tue Nov 21 18:17:12 EST 2023
;; MSG SIZE rcvd: 159
Then to test the query, again using the latest dig, try with dig +tls @192.168.29.251 example.org like this:
[2.7.1-RELEASE][admin@gateway1.lab29.anycorp.io]/root: dig +tls @192.168.29.251 example.org
; <<>> DiG 9.18.14 <<>> +tls @192.168.29.251 example.org
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 59694
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;example.org. IN A
;; ANSWER SECTION:
example.org. 60 IN A 93.184.216.34
;; Query time: 0 msec
;; SERVER: 192.168.29.251#853(192.168.29.251) (TLS)
;; WHEN: Tue Nov 21 18:20:08 EST 2023
;; MSG SIZE rcvd: 45
And finally, to test with a DoH query like this:
[2.7.1-RELEASE][admin@gateway1.lab29.anycorp.io]/root: curl -H 'accept: application/dns-json' 'https://anycorp-1zsq1h7h.2my.network/dns-query?name=example.org&type=A'
{"Status":0,"TC":false,"RD":true,"RA":true,"AD":false,"CD":false,"Question":[{"name":"example.org","type":1}],"Answer":[{"name":"example.org","type":1,"TTL":120,"data":"93.184.216.34"}]}
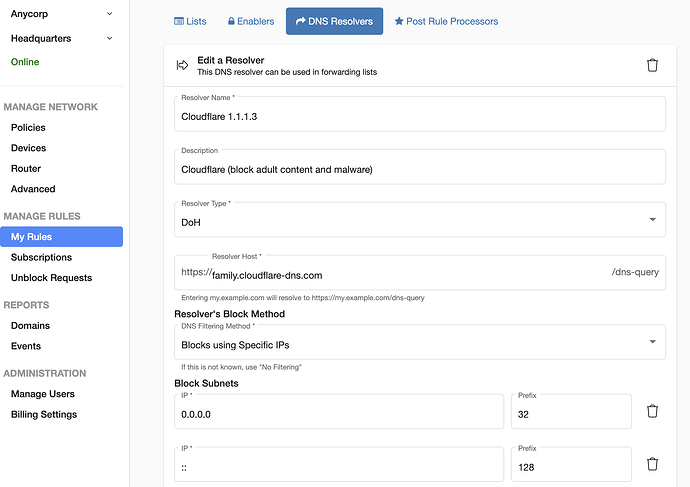
Upstreaming DNS Encryption
Each upstream Resolver set can be be defined using DoH or DoT. Here’s an example of setting Cloudflare 1.1.1.3 upstream resolver on the dashboard → My Rules → DNS Resolvers:
Conclusion
This DNS encryption stack offers legacy compatibility while offering best-in-class encryption for modern endpoints.