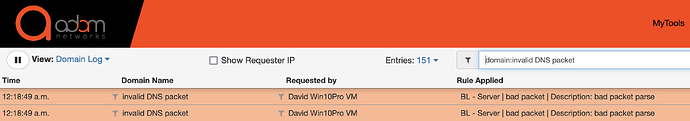
Your live log at mytools.management/log may display a domain name as invalid DNS packet like this:
This is an indication of a failed attempt to use TCP/UDP port 53 for tunnelling, although not DNS tunneling. Legacy networks often maintain an open port 53 for public DNS recursion purposes. If you’re seeing this on your network, you’ve successfully prevented port 53 tunnelling.
The most common scenario that leads to such log entries is an endpoint’s attempt to use port 53 to connect to a public service, but the NAT rule that forces DNS to adam:ONE® causes the re-direction, protection and exposure.