Article deprecated, see new one at adamnet.io/enablers
Purpose of Enablers:
adam:ONE and any Adam products that include DTTS (Don’t Talk To Strangers) sometimes require specific outbound firewall permissions since DTTS prevents any connection attempts that were not preceded with an allowed DNS query, or for applications that cache DNS queries beyond the TTL (time to live). We call such rule overrides “Enablers”.
Alternative ro Enablers on pfSense via Firewall Rules:
Enablers are rapidly-changing firewall rules which are executed dynamically on a per Policy basis. As such, they do not apply by default to all devices on a given interface/subnet, but only to devices assigned to Policies where such an enabler is turned on. On FreeBSD-based operating systems, this needs to be specified in kernel (pf), and, as a result, is not a scalable solution to do with a large amount of enablers.
Comparatively on Linux, NFQUEUE allows the decision-making process to be moved to user space and is therefore scalable to thousands of firewall rule changes per minute without impacting the overall performance. For this reason, Enablers are available on Adam products on the dashboard user interface, but only for Linux-based gateways, including ASUS router and Ubiquiti USG (Unified Security Gateway).
How to create DTTS bypass firewall rule:
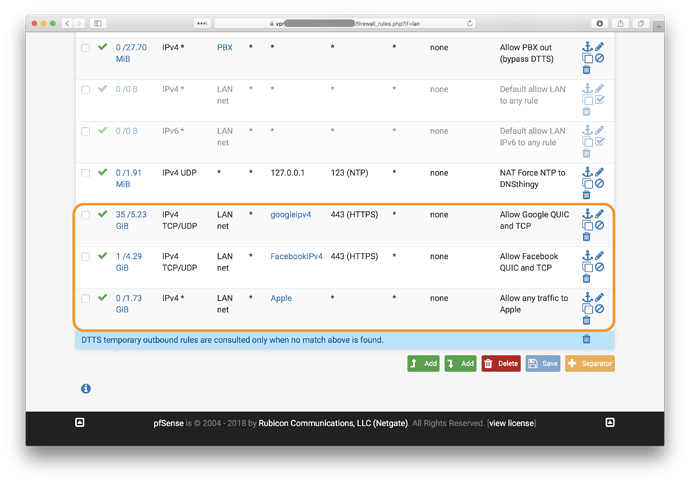
On pfSense web user interface choose Firewall → Rules and click on one of your non-WAN interfaces such as LAN and choose Add (the two options intuitively allow you to add the rule to the top or bottom of your rules):
![]()
Create as tight and narrow a rule as possible to eliminate the possible misuse of outbound channels that do not require valid DNS queries. Here’s a practical example of how Google, Facebook and Apple environments can be added:
NOTE: When rules are created like this in the pfSense UI, the Enabler on your dashboard UI should remain turned off.