The Zero Trust Model is the most secure way to control egress. For clarity, here are the elements of our zero trust model:
- Operating in whitelist mode (block all, allow some)
- Feature enabled (with appropriate plan): Don’t Talk To Strangers
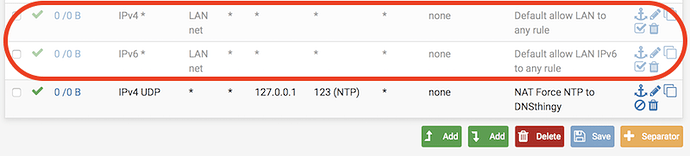
- Default LAN Allow All rule removed , or at least disabled
This approach ensures that no device can make an outbound connection of any kind, no matter the protocol, destination, or port. If you try to make a connection to say to one of Google’s IPs on TCP port 443, here’s what you’ll get:
curl https://216.239.38.120 … this connection fails with:
curl: (7) Failed to connect to 216.239.38.120 port 443: Connection refused
However, compare with this one:
curl https://www.google.com … this connection succeeds!
Another example:
PING 8.8.8.8 (8.8.8.8): 56 data bytes92 bytes from google-public-dns-a.google.com (8.8.8.8): Destination Host Unreachable
And yet this one…
$ ping google-public-dns-a.google.comPING google-public-dns-a.google.com (8.8.8.8): 56 data bytes64 bytes from 8.8.8.8: icmp_seq=0 ttl=59 time=16.982 ms
The difference is that when a successful (non-blocked) DNS query is answered, a temporary outbound firewall hole is opened for the period of the TTL.
Assuming you are starting from a default installation of mostly-default pfSense settings, here are your steps:
- Contact support to change your plan to allow for DTTS (Don’t Talk To Strangers) feature set
- Log into your dashboard → Advanced → Enable DTTS as shown here:
- Create (and enable) a LAN Firewall Rule to allow LAN DNS queries
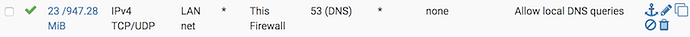
- Create (and enable) a LAN Firewall Rule to allow LAN port 80 access for the block page to function

- Turn off your pfSense default LAN Allow All rule (shown here as disabled as they are unbolded) or, alternatively check “Automatically manage DTTS rules in firewall” in Services → adam:ONE
: - Create any required Firewall Rules
Most environments that choose the Zero Trust Model end up with at least a few “misbehaving” apps that require special permission to make Internet-bound connections without preceding DNS queries. In cases like this, Enablers are needed as outlined here: https://adamnet.io/enablers
All attempted (but dropped) dns-less traffic can also be observed from your http://adam1.tools/log page by selecting TRAFFIC instead of DOMAIN log (top left corner of page).
To view real-time dynamic rules created by Enablers, run this at the command-line:
pfctl -s rules -a "userrules/enablers/*"
To view all real-time current rules, run this:
pfctl -s rules