In most pfSense® cases, unbound is used as a default DHCP server, which has great integration into local DNS as per the feature Register DHCP leases in the DNS Resolver. Unbound also automatically offers PTR DNS records for reverse DNS services. Many gateway and endpoint applications query PTR records regulary. In their absence, such applications perform sluggishly.
When also running adam:ONE® on the same gateway, these are the recommended best practices. This is what is deployed at new and renewed managed locations:
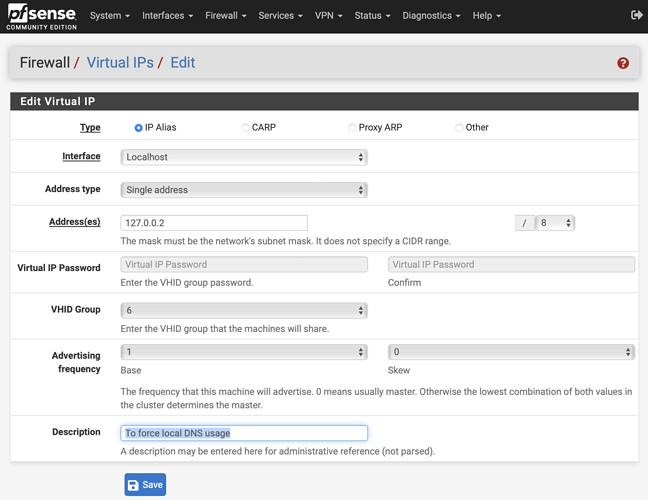
Prepare a localhost alias
Under Firewall → Virtual IPs → Add an IP Alias to interface Localhost like this:
We’re going to use this 127.0.0.2 alias for adam:ONE® only.
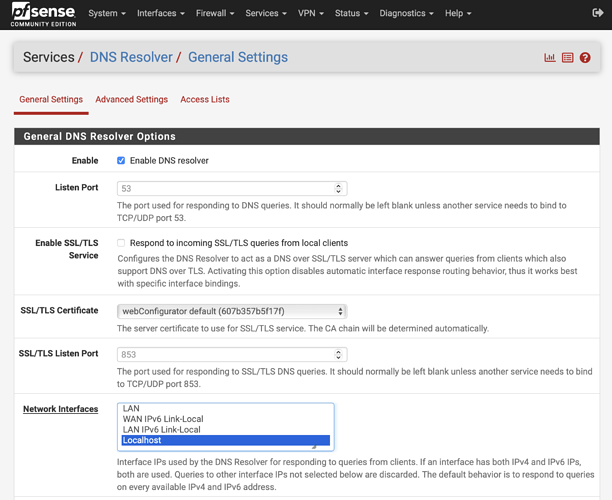
Bindings
- For unbound (Services → DNS Resolver), make sure the only interface selected is Localhost like this:
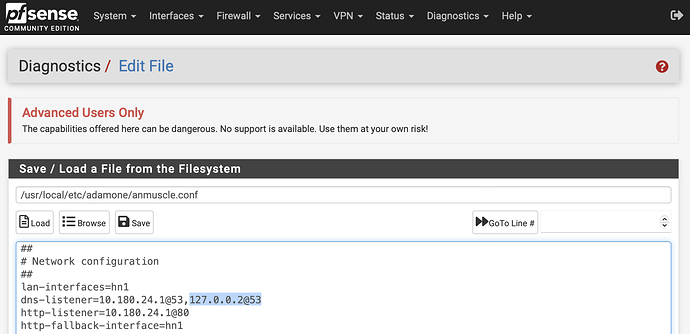
- For adam:ONE® make sure that
127.0.0.2@53is listed on/usr/local/etc/adamone/anmuscle.confas a dns-listener like this:
This can be done manually by editing the file or re-runningadamone-setup configurein an SSH session.
Restart both unbound and anmuscle services for proper service bindings.
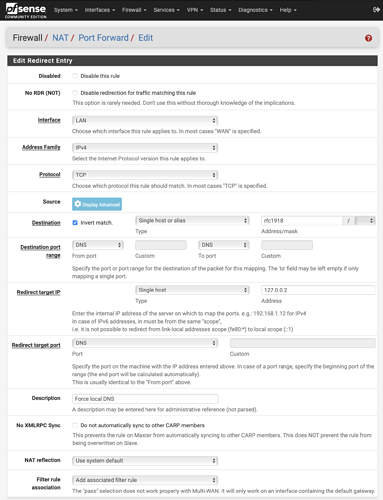
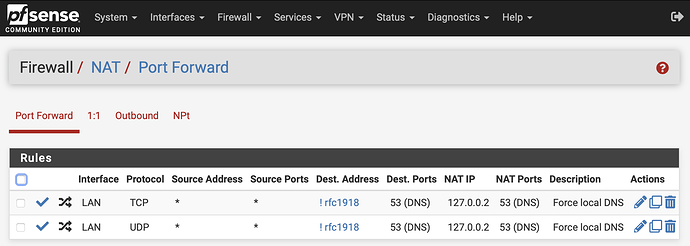
Using NAT to force local DNS
This step is optional, but if you want to retain elegant DNS functionality for internal devices that may have static DNS set to a public IP such as 1.1.1.1, there’s a way to offer the endpoints compatibility by forcing local DNS usage with two NAT hijacking rules like this:
The same rule can be copied, and just change Protocol of TCP to UDP so you end up with two hijacking rules like this:
In new community edition installations, rfc1918 alias is no longer built-in, but it’s easy enough to create it to include 10.0.0.0/8, 172.16.0.0/12 and 192.168.0.0/16 networks. Using this alias, makes it a nice universal rule that applies to any environment.
NOTE: Instead of applying the DNS hijack NAT rule to destination !rfc1918, an even better option is !This Firewall so that even if DNS/AD is in another network segment, it is forced to adam:ONE® instead.
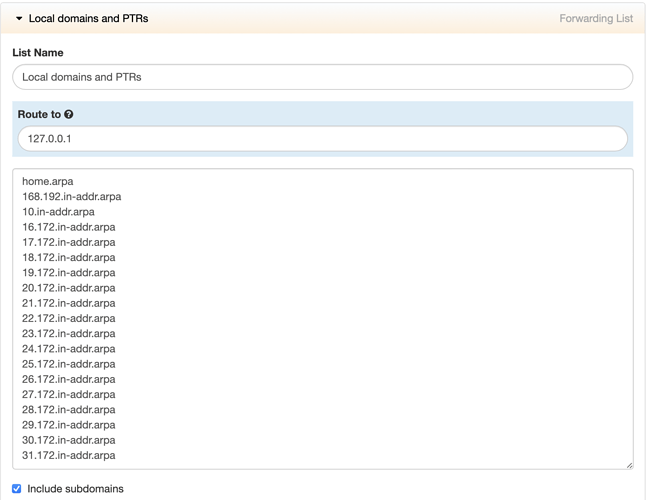
Forward rules to consult unbound on local domain
Finally, you want to make sure that adam:ONE® consults unbound for your local domain and PTR records by navigating to dashboard.adamnet.works → Rules → New List, create a new Forwarding List called Local domains and PTRs:
Adjust your list accordingly by replacing home.arpa with the domain you used and/or the domain suffix you offer via your DHCP server’s Domain option. The reason you still want to include all rfc1918 reverse DNS zones, however, is to prevent PTR record lookup leakage outside your network, so ensure that all of these are included:
168.192.in-addr.arpa
10.in-addr.arpa
16.172.in-addr.arpa
17.172.in-addr.arpa
18.172.in-addr.arpa
19.172.in-addr.arpa
20.172.in-addr.arpa
21.172.in-addr.arpa
22.172.in-addr.arpa
23.172.in-addr.arpa
24.172.in-addr.arpa
25.172.in-addr.arpa
26.172.in-addr.arpa
27.172.in-addr.arpa
28.172.in-addr.arpa
29.172.in-addr.arpa
30.172.in-addr.arpa
31.172.in-addr.arpa
That will enable tight integration between adam:ONE® and unbound, making use of the DHCP automatic forward and reverse DNS names (PTR records) for local network device names.
And finally, enable the Rule on each Policy: